Properly assessing risk through a risk management framework program is a vital part of establishing a security posture and a “must-have” for a company. Risk assessment steps are as follows: Categorize, select, implement, assess, authorize, and monitor are the steps in the NIST framework, and along with risk assessment and analysis, the program helps support the policies set by executive management and show due diligence and due care in the safeguarding data and systems. The primary goal of risk management is to reduce risk to an acceptable level. The elements of risk are asset, threat, vulnerability, exposure, risk, and safeguard. “Threats exploit vulnerabilities, which results in exposure. Exposure is a risk, and safeguards mitigate risk. The threat is mostly human factors.
An internal threat can cause a lot of damage to the company. The internal threat can be voluntary or non-voluntary. An insider threat is a security threat that originates from within the organization being attacked or targeted. These threats often occur from an employee of an organization or enterprise. Sometimes the employees may not be a current employee but a former employee, board member, or anyone who at one time had access to confidential information from within an organization (Lord, 2018). Every employee is a potential internal threat. The primary personnel that can cause significant danger and destruction are the Executives, Senior Managers, and System Administrators.”.
Organized crime might be the source leading to insider threats. An internal person, in that case, is working for the interest of other organizations or institutions against the company interest and long-term property. Different approaches can be taken to address the insider threat. For example, a formalized program needs to be developed and embraced by top management for a successful security Management Framework. The Risk Management Framework will help the company integrate the control system for healthy information security. In our previous risk profile, it is stated, “Insider threats can occur as a result of an individual using their access to sensitive information for personal, political, or financial gain. An insider who has aligned themselves with third parties can operate on their behalf to gain access from within the network of trust and share sensitive information (Lord, 2018).”
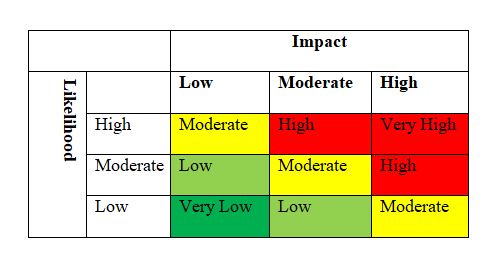
A successful data exfiltration causes by insiders is frequently reported to be one of the most important in a cyber breach. Most often, the company is focused on detecting an outside threat; they neglect insider threats that have more chances to be successful and be more damaging to the company. Most intrusion detection tools focus on detecting external threats. The organization system may be compromised by bypassing defensive measure due to the fact that the instructor is knowledgeable of the defensive system. He also knows the company secret and can sell it to the competition. It is crucial for the company to rate risk in order to understand the likelihood of occurrence. The Risk and Threat Matrix, map the risk findings based on the impact of the risks on the mission-critical systems and the likelihood that a threat events may harm the company assets. NIST 800-37 and NIST 800-30 can be used to determine the risk level. Determining risk level implied classifying assets into systems according to their functions. The most critical asset will end up with a higher rate if the system connection is complex and have high exposure to an internal threat. The classification arrived at the High, Medium, and Low-risk level as it shows in the risk level guidance table below by multiplying the risk/threat impact with the probability/likelihood of such risk occurring. The below table describes the risk assessment table
Table 1: Assessment Scale – Level of Risk (Combination of Likelihood and Impact)
Alice Ouedraogo, MS
Reference
NIST Special Publication. (March 2011). SP 800-39. Retrieved from
https://ws680.nist.gov/publication/get_pdf.cfm?pub_id=908030

